Data Breaches – Lost Devices a Leading Cause
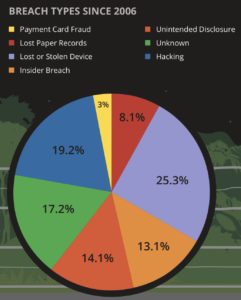
Based on a report from Bitglass, more than 1/4 of all data breaches over the past decade involved a lost or stolen device containing corporate data. This exceeded the 13% due to insiders, 14% due to unintended disclosure and 19% due to active hacking.
Some of these numbers can be a bit misleading from the perspective of data actually in the hands of malicious parties. The costs, however, remain real in any case and the potential for catastrophic harm to a business can be alarming.
Data Breaches – The Reports
Laws regulating publicly traded companies and many industries require disclosure of a potential breach, regardless of whether the information was actually accessed. Responsible companies report the potential for a breach when devices containing data are lost, even if there is no evidence that malicious parties made use of the data. This may lead to inflated numbers in some reports, due to the largely unknowable gap between potential and access access to breach data.
Data Breaches – The Cost

Estimates from one recent report show the average cost per breach has risen to over $3.8 million, or about $148 per record lost or stolen where the record contains personal, confidential or otherwise sensitive information.
If you are a security professional responsible to preventing these breaches, you probably already have a few sleepless nights even if your company has not suffered a breach on your watch.
If you are a corporate executive estimating the costs of a breach, you may be hearing a career-limiting sucking sound which is rapidly draining the bottom line in your nightmares.
Your best strategy in either case is to give careful thought to your security preparedness. The potential cost of failure is so high that it should be relatively easy to justify a highly qualified team and ongoing activities to plan, test, improve and retest all aspects of your security.
Leave a Reply
You must be logged in to post a comment.